Anchor
Glossary
One Page Primer
Slides Soft ChipsTM Blogs
Book
Mesh ACG
SlideShare
Linkedin Bio
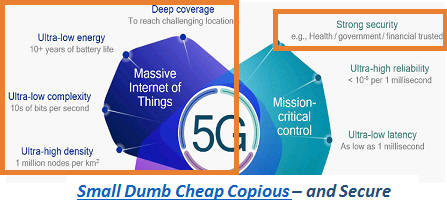

Fig.1
Above Left. Key
Challenges to “
Massive
IoT” are Energy, Complexity, Density + Security.
Fig.2
Above Right. Nature's Massive IoT uses light, innately secure receiver biased messaging.

Fig.3
Consumer: Medical Sensor Patches ->
Makes Data
Logs -> Delivers to Carrier Pigeons -> Cloud -> "Edge" Intelligence

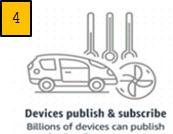
Fig.4
Enterprise: "Imprinted" Sensor Patches
-> Makes Data Logs -> Delivers to Pigeons -> Cloud -> "Edge" Intelligence
 The Rationale
behind
Small Dumb Cheap Copious
Innately Secure
The Rationale
behind
Small Dumb Cheap Copious
Innately Secure
Over
next decades, billions of IoT devices will be monitoring
farms, forests, oceans, and other natural resources with
sparse and intermittent cloud connectivity. As IIoT
becomes more autonomous,
connectivity is both sufficient and ubiquitous. Edge sensors
may now provide logs for intermittent pickup and delivery.
IPV6 protocol is heavy - intended for humans.
In sharp contrast, Nature’s
IoT messaging is terse, cryptic,
receiver-oriented and self-classifying.
And intentionally lightweight - like
Pollen.
Taking cues from
Nature, “Chirps” were developed for
SPAWAR
for stealth messaging across global networks.
Sharp
Corp. licensed
a version for Asia. In this
Cloud->Edge thinking, Soft Chips
providing Edge Intelligence are
imprinted to send trusted
ground truth data logs - on cloud managed
schedules and RF channels.
Soft Chips just need wireless serial modems. All radios
can or do support
that. Chirps thus piggyback on existing radios and protocols
and widely used encrypted, trusted and ubiquitous messaging
infrastructure - SMS, WhatsApp, Email on connected devices. If
phones don't support desired radio frequencies (for range,
obfuscation etc) then USB powered
receivers are a simple fix. The phones just need protocol
handlers. Iphones and Ama
zon
Sidewalk networks - currently walled gardens - now support lighter
versions of
AirTagTM for mobile asset tracking. Simpler, lower cost and low power
devices engender Massive IoT. Security is addressed
next.
 Soft Chips, Security and CHIPS initiatives
Soft Chips, Security and CHIPS initiatives
Soft Chips embodiments are intended
for dual use (military and industrial) since the security is in
the imprinting services provided by trusted hosted services.
Also the ends of wireless modems at the Edge are "paired" - know of each others' schedules and RF channel usage
and handshake protocols. In other words, the probability of bad
actors intercepting terse - intentionally stealth-like
messaging is low simply because the combined probability of
multiple variables all being detected correctly is
infinitesimally small- and the variables are being changed
with each encounter.
When pigeons arrive, data
logs are transferred based on
imprinting protocols. Schedules and
protocol framing are private and changed - using
temporal keys and
frequency hopping. Innately Secure.
End-to-End and
Zero Trust.Our current
Edge->Cloud thinking around End-to-End security and
trust is driven by onerously "heavy" encryption - which
conflicts with low power usage and cheap hardware objectives.
Based on Nature's consensus approach to "small dumb cheap
copious", corroborated edge intelligence from multiple sensors
(a sensor grid) leverages many sensing devices, operating on
different "channels". See
Image.
Total Cost of Ownership plummets with economies of scale driving
down dense sensor grids deployed in remote or
hostile areas and for many applications.
In our polarized world, governments and military deploy edge
devices
imprinted by them to provide womb-to-tomb ground
truth verification. Sensitive data is not sent over foreign
networks and equipment. Covert networks over trusted devices
are used. Business is war watered down. Today, all Global
enterprises and Regulatory agencies run on federated “Clouds”
and expect authentic data from their assets on the ground.
Our AI systems need large, reliable and corroborated data logs
- else its all
GIGO.
CHIPS initiatives - "integral to America’s economic and
national security" benefit from collaborative sharing of
trusted, previously
walled private gardens.
Global scale challenges mandate Globally Relevant Edge à Cloud
solutions.
 Global Impact of
Simple Devices Speaking Simply. -> Cloud
Orchestration Models
Global Impact of
Simple Devices Speaking Simply. -> Cloud
Orchestration Models
Today’s
last mile is crippled by fractured
MAC-centric
protocols: all un-scalable solutions.
The
Cloud Orchestration model cuts Gordian knots in Fig. 1 and
unleashes the full power of IIoT.
Challenges in Fig. 1 are
exacerbated for currently un-connected Legacy machines.
Industrial versions of Sensor Patches
may
now be copiously and non-invasively - attached to un-connected
legacy remote assets for their predictive maintenance -
driving new efficiencies in managing the Edge.
Chirpers just need wireless serial modems. All radios support
that. Chirps thus piggyback on existing radios and protocols.
If Chirpers need to use an unsupported radio, USB powered
receivers are a simple fix. Iphones just need protocol
handlers (at the radios). Iphones and Amazon
Sidewalk - previously walled gardens - now support lighter
versions of
AirTagTM . Simpler devices - e.g. Soft ChipsTM - engender Massive IoT.
1. Small. Small
Radio Power Usage and Footprint - Long Battery life.
2. Dumb. Limited Ant-like
processing capabilities - but re-programmable.
3. Cheap. Intended to be
produced in billions - since multi-use
4. Copious. Intended to be used like Smart
Dust - dense ground truth verification.
5. Secure. Imprinting process -
end-to-end - is innately secure. Also see Provenance
6. Organic. No central standards needed.
Modem based Chirp protocol Enterprise specific.
7. Agnostic. Chirps radio and protocol agnostic.
Can coexist with other protocols.
Edge->Cloud thinking thus shifts to a more sustainable,
scalable, secure Cloud->Edge thinking:
1. Cloud Orchestrator -> Trusted Pigeon -> Imprints
Chirp with new Logic, Schedules.
2. Chirper -> Runs Logic -> dumb wireless modems ->
Receiver Radios on Phones, Drones etc.
3. Receivers harvest Chirps -> Add tagging -> Pub/Sub
messaging -> Cloud Subscribers.
4. Chirpers with Ant-like imprinted logic run on
billions of chipsets -> “Massive IoT”.
Key Conjectures when thinking shifts from Edge->Cloud to Cloud->Edge thinking:
1. Global-Scale “Edge” challenges are: simplicity,
cost, energy & (as always) security.
2. Chirpers don’t need heavy OSI stack -> minimal power
and cost for connectivity.
3. Software Defined Networking for the Edge -> Moves
Chirping Intelligence to Cloud.
4. Trusted walled gardens become globally relevant
through our imprinted chipsets.
5. Massive IIoT - with no legacy systems left behind - burgeons.
 Soft ChipsTM
Exemplary Embodiments
Soft ChipsTM
Exemplary Embodiments
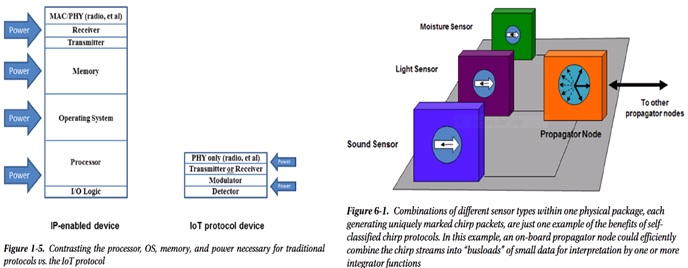
Fig. 5. Left. Soft Chips don’t need the full
OSI stack -> minimizing power and cost.
Fig. 6. Right. Exemplary Soft Chip are packaged sensors +
UART based wireless serial modem.

Fig. 7. COTS available
Development Tools, 16 bit MCU and
Simple, Cheap Sensors to engender Soft Chips.
Soft Chips and its low cost and power
embodiments
may be deployed with little or no electricity, in developing
regions or where remote natural resources reside - the "Edge".
Platform as a service providers -
PaaS - will use carrier pigeons (cars, drones) to forward
chirps for Edge Intelligence
and
SLA compliance.
Chirp Networks with imprinted
edge intelligence may then glean trends from
sensor data collected within food systems, agriculture
production, factory distribution, and climate preparedness. Logically contiguous
clouds cross over previously walled garden boundaries -
engendering Massive IIoT which can now support:
A. Global Health Diseases can spread like wildfire in dense
unsanitary make shift housing in slums and refugee camps. We
"chip" our pets so we can track them. We may also track
disease spread through small dumb cheap and most importantly
copiously used Sensor Patches.
A USB or BLE modem paired to phones readily serve as
carrier pigeons for global scale regulatory and monitoring
agencies - proactive preparation for future epidemics.
B. Legacy Assets are unconnected - they were not designed
initially to be networked. Sensor patches - attached
non-invasively can monitor sounds, temperature, vibration of
rotating machinery. Actionable intelligence gleaned by AI
driven pattern analysis - operating on huge datasets - will
drive new efficiencies in remote asset management - with no
legacy assets left behind.
C. Forest Fires and Early Warning Systems. Soft Chips are intentionally dumb - to
minimize power consumption and cost. Their radios can listen,
chirp, or relay (listen then chirp on non-interfering RF
channel or time interval. A Chirper Grid then rapidly spreads
the word so to any available carrier pigeons (patrol drones,
park rangers), saving billions.
D. Global Food Systems and their management. Data
logs sent over SMS from Africa feed data lakes and drives new efficiencies.
E. Military uses - covert mobile asset tracking and intrusion detection in
DMZ
or hostile regions (has been field tested).
F. Asset Tracking from "birth". Establishing
Provenance - where raw materials are sourced - and audit
trails for logistics supply chains is increasingly relevant
today. Soft Chip products are
imprinted – establishing provenance to “Mother”. On power
up chirp devices first scan/listen for “Mother” on private
channels and cryptic protocols. Receiver radios on phones or
drones respond to imprint the devices. If RF interference
occurs, they are directed to to other channels schedules etc. Imprints provide a
reliable
end-to-end trusted system.
Soft Chips have a minimal - but extensible - base vocabulary: Send,
Listen, Relay, Log. Transmissions are either scheduled - e.g.
Cron - or
trigged by events - a listener on activated sensor on a
Sensor PatchTM
This Extensible Soft Chips family addresses multiple military
and industrial -
dual use - applications.
 Soft ChipsTM
Terse Protocol Framing Example. (Leveraging SMS
like messaging services)
Soft ChipsTM
Terse Protocol Framing Example. (Leveraging SMS
like messaging services)

A minimal viable Soft Chip work flow may use
SMS as message broker and BLE/USB on pigeons to store and
forward.
More
Consider a potential use case for a farmer in rural Africa.
His phone has no connectivity in the field where the sensors
are. A store and forward mechanism is needed – see this
email based thin device for Asian rural distribution
chains. We also wish to leverage SMS like free messaging
services so we limit the total payload to 160 bytes
and for SMS
transmissions. There will also be tagging at the Smart phone
application end before it is transmitted to SMS message brokers - when the
farmer has connectivity. We thus further limit data log
payload to not exceed 110 bytes, with 10 bytes reserved
for Chirp-ID etc. The 100 byte data log will be sent on SMS, so we may
further restrict it to ASCII and CSV-like format.
For the 100 bytes payload (the data log) our options are based
on how many samples and each sample size in bytes :
#Samples : Sample_Size_in_Bytes: 100:1, 50:2,
25:4, 20:5, 10:10, 5:20, 4:25,
2:50, 1:100 (100 bytes each).
Thus 4 sensors, each providing 1 byte may be sampled 25 times
during pigeon pickup sessions. This specific Chirp
payload framing is thus fleshed out to be 25 samples of
|Sensor_1|Sensor_2|Sensor_3|Sensor_4| = 25 *4*1 bytes.
This is generous because 2 bits (00 01, 10, 11 )
can define “black or dead”, “red”, ”yellow”, “green” mapping
to programmed sensor data ranges. 4 sensor feeds can be
condensed to one byte (8 bits). Edge intelligence can be
terse yet meaningful- especially in
receiver-oriented communications. .
When pigeons arrive, data
logs are transferred based on handshaking supplied in the
imprinting protocols- and could be as simple as an
obfuscated version of Chirp-IDs. Recall schedules and
protocol framing are private and can be changed each
trip - using
temporal keys and
frequency hopping. Innately Secure.
After data logs are
delivered, the data log is erased and effectively a soft
reboot begins the next data logging schedule - which may
include a new programs or framing.
The soft chip may not have GPS to conserve both cost and
power, but pigeons may - then time/location are synched.
Mobile asset tracking at this level of granularity may
suffice.
The farmer transfers the data log (110 bytes) from the pigeon
to apps on his phone with BLE pairing between his phone and
the BLE radio on the pigeon. The phone app can add GPS and
time stamp tags and eventually forwards it to message brokers
- SMS, WhatsApp etc. These trusted
community networks may include oversight agencies
who rely on remote ground data to drive forecasting etc.
A minimal viable - and self sufficient - product emerges which may
also leverage existing BLE connectivity, already in use for indoor
IoT to connect with BLE mesh on local WLANs. The
farmer's phone may thus use other phones in the network to
connect to cloud services.
Consider now two
WhatsApp accounts on the farmers phone. One is admin
protected and provides programs and schedule templates.
The phone app adds jitter settings so soft chips avoid
collisions and generates new imprints for all Soft Chips on
the farm- a poor man's Cloud Orchestrated Model. The
pigeon- like postal workers - carry community "mail" and
distributes it. Data logs from soft chip grids,
collected through the region are sent to another SMS or
WhatsApp account to collectively provide actionable
intelligence available to digital and human subscribers
- operating at a Globally relevant scale. Thus two
messaging accounts, an intermittently connected device and
store-and-forward pigeons support dense sensor
grids relevant to food supply, climate preparedness, asset
tracking etc.
 Cloud
Orchestration Models and Benefits. (A recap)
Cloud
Orchestration Models and Benefits. (A recap)
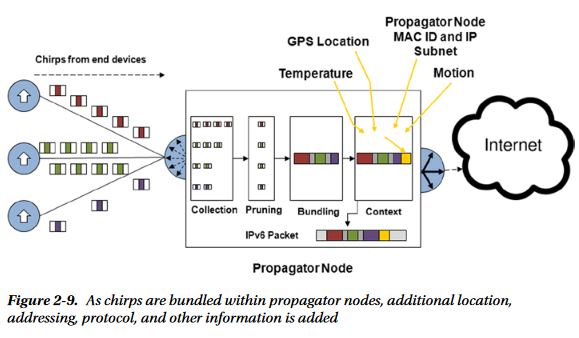

Fig.8 Left: Apps on receiver phones/drones Prune, Tag and
Bundle Chirps for the Cloud.
Fig.9 Right: Cloud Orchestration Model for application aware
networking and work flow scheduling
More
Cloud->Edge thinking drives a new look at Global Scale
Edge Connectivity:
Shifting radio intelligence to the receiver and cloud is
functionally equivalent to
CSMA/CA
and
DCF
for minimal power Edge. Human driven RF chatter required
smarts in phones operating in congested, dynamic RF. This
drove
BLE devices to use
MAC based protocols that phones
understood.
In military environments RF patterns were
learnt, predicted and drove schedules & channels.
Incumbent Edge Based processing for Collision avoidance is
inherently inefficient see
Backoff for reasons why. In contrast Cloud driven
collision avoidance has processing power for all devices under
its care. For more please see
Evolutionary Networks.
Radio Agnostic: Chirp protocols are primitive - all
radios support serial modems. Chirp versions of Apples' Airtag
may run on existing radios. The Chirp is tagged by the carrier
pigeons and the imprinting approach is vendor neutral. Apple
and Amazon networks may use existing radios, now Chirp aware.
Radio not supported by either family of devices can be USB
attached - a simple fix. The networks are now extended for
both.
MAC-Less Protocols are light. Chirp packets use topic
based addressing - a byte suffices to distinguish 255 distinct chirp
species operating at the same time and RF channels. Compare to
IP headers of 40+ bytes.
Imprinting. Chirp products are
imprinted – establishing provenance to “Mother”. On power
up chirp devices first scan/listen for “Mother” on private
channels and cryptic protocols. Receiver radios on phones or
drones respond and imprint the devices. If RF interference
occurs, the cloud directs them to other channels or schedules
- teaches them new tricks. Imprints provide an
end-to-end trusted system.
Establishing provenance of sourced materials - which tree in
which forest - has to come from imprinted tags that follow the
tree from the forest to the lumber yard and onwards to Home
Depot. Provenance chains kick in when the tree is first felled
- with re-usable RFID++ tags and then fans into all her
finished goods.
Deployment Costs Plummet. The cost of
Dual
Band radio is $20. 433 MHz Wireless modems are 10
cents.
MAC based radios use 45 bytes to transport a 4 byte data
packet. Chirpers do it in 5 bytes with one byte for ID
tagging. And
CSMA/CA
are inefficient compared to scheduled broadcasts. Coin
batteries can now last decades.
Cloud managed Scheduling Logistics. Control systems need timely inputs from the
field – this is back scheduled from when carrier pigeons
arrive, the size of the data logs to be stored etc. The entire
data logistics supply chain is visible and used to imprints
both sensors and pigeons. The Enterprise tunes it to avoid RF
interference by changing channels and schedules.
Discovery. Digital version of
Bird Call registries will empower discovery of hidden
corroborating intelligence.
Symbiotic signaling - as in Nature - is currently lost.
More.
Standards. Nature's Massive IoT grew organically,
managing collision domains in time and region by evolved
differentiated "tunes". The Chirp protocol does not need
standards bodies -
for these reasons.
Security. Chirp protocols are
receiver oriented. Cloud driven scheduling provides
dynamic collision avoidance in both time and RF channels. Thus
both the USB powered receiver radio pigeon unit and the
chirpers have to know both when, where or how to chirp- both
being imprinted by trusted hosted
PaaS.
Swarm Intelligence was one objective in
Small Dumb Cheap and
Copious. Copiously spread Soft Chips –
like aerial crop dusting - will drive new efficiencies in
addressing climate, food management, regulatory concerns,
mobile asset tracking, all requiring trusted Edge Sensors and
globally dense ground coverage.
Global Relevance. Chirp NetworksTM are device
level authenticated. They are
logically contiguous - over previously walled garden
boundaries. Thus Chirps picked up by a receiver Apple Phone
(with USB Modem) is propagated via Amazon trucks - because
these devices have been opted in by federated hosted services.
 Summary
and Conclusion.
Summary
and Conclusion.
The rapidly accelerating confluence of
Distributed AI with Software Defined Networking (SDN) prompted
Cloud Orchestration Models. Chirp networks
coalesce to be
logically contiguous across walled
gardens.
Cheap, Copious, Global Scale Connectivity then drives new -
currently impractical - efficiencies.
Soft Chips is a "natural" alternative to key challenges in
remote edge asset management.
Bio Slides.
1. Today: Radios with
BLE,
Zigbee,
Lora
=> Fractured Markets and Silos ==
Not Massive
versus
2. Chirp: Modems with Imprinted Pigeons
=>
Contiguous Clouds and
Pub/Sub
(e.g. SMS, AWS.. ) ==
Massive and Trusted.
 Addendum: Our
Robotics and Supervised Autonomy Focus
Addendum: Our
Robotics and Supervised Autonomy Focus
Meshdynamics' founder
Francis
previously started
Advanced Cybernetics Group.
ACG was contracted by the US Air Force and NIST to work on
Supervised
Autonomy for remote robots (telerobotics).
When it became apparent that last mile connectivity had its challenges, Meshdynamics
was formed to develop robust real-time connectivity solutions for
semi-autonomous military machines.
In 2002, SPAWAR and USAF funded a multi-year NRE contract for
us to develop a distributed, fault-tolerant device/protocol
agnostic mesh control layer for use on edge military gear that
included stealth “sensor dust”.
Taking cues from Nature, our work began with tree-based control networks then moved
to ants (mobility), pollen (broadcast storms for propagation) and finally birds (Chirp
and Chirp protocols). This
journey
is driven by overlapping
interests in Edge and Cloud.
1982-2002 Robots > +Sensors > +Tele-robotics > +Supervised
Autonomy (Critics)
2002-2012 Time Sensitive Networks for remote machines
(scalable mesh networks, Disruption Tolerance, Stealth)
2012-2022 Re-thinking the Internet of things, Proving Cloud
Orchestration models
 Addendum: Introduction, “Rethinking the Internet of
Things”, Intel Press, 2013.
Addendum: Introduction, “Rethinking the Internet of
Things”, Intel Press, 2013.
I didn’t set out to develop a new architecture for the
Internet of Things (IoT). Rather, I was thinking about the
implications of control and scheduling within machine social
networks in the context of Metcalfe’s Law. The coming tsunami
of machine-to-machine interconnections could yield tremendous
flows of information – and knowledge.
Once we free machine social networks (comprised of sensors and
other devices) from the drag of human interaction, there is
tremendous potential for creating autonomous communities of
machines that require occasional interaction or reporting to
humans.
The conventional wisdom is that the expansive address space of
IPv6 solves the IoT problem of myriad end devices. But the
host-to-host assumptions fossilized into the IP protocol in
the 1970s fundamentally limited its utility for the very edge
of the IoT network.
As the Internet of Things expands exponentially over the
coming years, it will be expected to connect to devices that
are cheaper, dumber, and more diverse. Traditional networking
thinking will fail for multiple reasons.
First, although IPv6 provides an address for these devices,
the largest population of these appliances, sensors, and
actuators will lack the horsepower in terms of processors,
memory, and bandwidth to run the bloated IP protocol stack. It
simply does not make financial sense to burden a simple sensor
with the protocol overhead needed for host-to-host
communications.
Second, the conventional implementation of IP protocols
implies networking knowledge on the part of device
manufacturers: without centrally authorized MAC IDs and
end-to-end management, IP falls flat. Many of the hundreds of
thousands of manufacturers, building moisture sensors,
streetlights lack the expertise to implement legacy network
technology in traditional ways.
Third, the data needs of the IoT are completely different from
the global Internet. Most of the communications will be terse
machine-to-machine interchanges that are largely asymmetrical,
with much more data flowing in one direction (sensor to
server, for example) than in the other. And in most cases,
losing an individual message to an intermittent or noisy
connection will be no big deal. Unlike the traditional
Internet, which is primarily human-oriented (and thus averse
to data loss), much of the Internet of Things traffic will be
analyzed over time, not acted upon immediately. Most of the
end devices will be essentially autonomous, operating
independently whether anyone is “listening” or not.
Fourth, when there are real-time sensing and response loops
needed in the Internet of Things, traditional network
architectures with their round-trip control loops will be
problematic. Instead, a way would be needed to engender
independent local control loops managing the “business” of
appliances, sensors, and actuators while still permitting
occasional “advise and consent” communications with central
servers.
Finally, and most importantly, traditional IP peer-to-peer
relationships lock out much of the potential richness of the
Internet of Things. There will be vast streams of data
flowing, many of which are unknown or unplanned. Only a
publish/subscribe architecture allows us to tap into this
knowledge by discovering interesting data flows and
relationships. And only a publish/subscribe network can scale
to the tremendous size of the coming Internet of Things.
The only systems on earth that have ever scaled to the size
and scope of the Internet things are natural systems: pollen
distribution, ant colonies, redwoods, and so on.
From examining these natural systems, I developed the
three-tiered IoT architecture described in this book: simple
end devices; networking specialist propagator nodes, and
information-seeking integrator functions.
In these pages, I’ll explain why terse, self-classified
messages, networking overhead isolated to a specialized tier
of devices, and publish subscribe relationships formed are the
only way to fully distill the power of the coming Internet of
Things.
Francis daCosta
LinkedIn
Santa Clara, California, 2013










