|
||
|
|
||
|
Anchor
Glossary
One Page Primer
Slides Soft ChipsTM Blogs
Book
Mesh ACG
SlideShare
Linkedin Bio 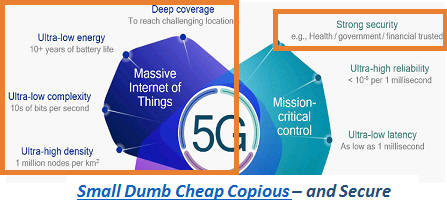
Fig. 1. Left. Key Challenges to “Massive IoT” : Energy, Complexity, Density + Security. Fig. 2. Right. Nature's Massive IoT uses light, power constrained, cryptic receiver biased messaging. 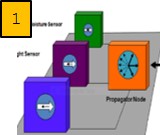
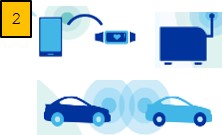

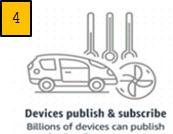 Fig. 3. Soft ChipTM - Imprinted Sensor Patches -> Data Logs -> Pigeons -> Cloud -> Intelligence Fig. 4. Left. Logically Contiguous Cloud - where the Cloud joins "broken" connections. Fig. 5. Center Cloud Orchestration Model - where RF channels, task schedules driven by cloud intelligence. Fig. 6. Right. Soft ChipTM Work Flow - How Edge Intelligence is harvested by Cloud Subscribers. Enlarge ________________________________________________________________________________________________________ This glossary explains terms - some unfamiliar, some being used differently - to describe the Cloud Orchestration Model and Soft Chips - Trusted Edge Intelligence operating semi-autonomously in remote, harsh, hostile regions. _________________________________________________________________________________________________________ Abstracted Internet. A radio hardware and radio protocol abstracted world where cloud servers manage last mile network topology, RF channel diversity and the timing of when Edge devices speak, listen and relay. This timing is based on application awareness - when Edge sensory data is needed to be delivered. Ant-like. See also Deterministic Finite Automata Specific Purpose Reprogrammable behaviors. Back Off devices must be polite -listen first and wait for silence before talking. This uses more power and processing than simple modems that are listen on cloud scheduled time reservation slots like TDMA. The Cloud Orchestration model sets RF channels (to avoid RF interference) and scheduled time reservation slots. Carrier Pigeons, Pigeons, Propagators. The packet transport from rudimentary edge protocol to cloud. RFID readers encapsulates the raw signals into a useful format. Similarly Pigeons, over a rudimentary - and legacy supported - serial modem, take in Chirp packets, tag and prune them and put them on a shuttle bus to interested subscribers. Illustration. Chirps. Taking cues from Nature, (digital) Chirps are terse, cryptic receiver oriented messaging. Birds chirp - and while we can distinguish species of birds we do not understand the meaning. Distinguishable yet Undecipherable. Innately secure. Combined with imprinting at birth, this ensures end-to-end security. Chirp Devices - are imprinted – establishing provenance to “Mother”. On power up chirp devices first scan/listen for “Mother” on private channels and cryptic protocols. Receiver radios on phones or drones respond and imprint the devices. If RF interference occurs, the cloud directs them to other channels or schedules - teaches them new tricks. Imprints provide an end-to-end trusted system. See Pollen and its use cases. Cryptic. Chirps are cryptic 1-2 bytes – compare to IPV6 40+. Schedules ensure collision avoidance. Ossified CSMA/CA not needed.+ RFID is a static GUID identification scheme. The tags is applied to boxes in transit and when energized, transmit a code to the reader. Cloud Orchestration. See Illustration, Fig 5. The model manages collision avoidance proactively by: . RF channel diversity and network topology management - as in scalable O(nlogn) tree structures. More . Cloud application awareness - when data from the edge is needed - time window of relevance. More . Addressing conflicting objectives or RF interference by re-imprinting RF channel and schedules. More Cloud->Edge Thinking. Shifting radio intelligence to the receiver and cloud is functionally equivalent to CSMA/CA and DCF for minimal power Edge. Human driven RF chatter required smarts in phones operating in congested, dynamic RF and this drove BLE etc. devices to use MAC based protocols. In non-urban spaces, RF patterns were learnt, predicted and drove schedules and channels. More: Evolutionary Mesh Networks) Collision Avoidance. Shifting radio intelligence to the receiver and cloud is functionally equivalent to CSMA/CA and DCF for minimal power Edge. Human driven RF chatter required smarts in phones operating in congested, dynamic RF. This drove BLE devices to use MAC based protocols that phones understood. In military environments RF patterns were learnt, predicted and drove schedules & channels. Evolutionary Networks. Incumbent Edge Based processing for Collision avoidance is inherently inefficient see Backoff for reasons why. In contrast Cloud driven collision avoidance has processing power for all devices under its care. Discovery (Fellow Chirpers). Digital version of Bird Call registries will empower discovery of hidden corroborating intelligence. Symbiotic signaling - as in Nature - is currently lost. More. Design Implosion in this context relates to reducing the design search space by breaking log jams between conflicting objectives. For example low power usage consumption is difficult with the processing power needed for high security in an Edge->Cloud paradigm. Shifting to Cloud->Edge reduces the variables and such conflicting objectives, simplifying the problem space. Edge. In this context it implies low power consumption IIoT devices operating in remote, harsh, hostile or under-developed regions e.g. where our natural resources are mined or cultivated. They have: . Need for minimal power usage - use terse protocols and infrequent data log deliveries. . No one single piece of sampled data is critical - delivery that don't sometimes happen is OK. . Regions serviced are remote - carrier pigeons visit infrequently and schedules may slip. . Data logs delivered on a best efforts intermittent connectivity basis and it suffices. . The primitive Ant-like intelligence is reprogrammable by Cloud agents - carrier pigeons. Edge->Cloud thinking. Last mile connectivity is challenging in logistic supply chains because pick up and delivery are predicated on available bulk transport (planes, trucks, ships) and distribution from hubs. As a result IoT radios use congested and short range BLE Protocols. Phones - Ubiquitous Pigeons - support it. The cost is "heavier" hardware and power usage. This is edge to cloud thinking and is not sustainable. CSMA/CA and DCF are inherently inefficient - the radios are "polite" and listen/wait till the shared RF medium is silent and available - see Backoff. Conversely Serial Modems are "dumb" - the external environment ensures the time and RF Channel reservation slots- the orchestration of RF chatter is cloud managed. 1. Today: Radios with BLE,Zigbee,Lora=>Proprietary Gateways=>Fractured Markets and Silos=>Not Scalable. 2. Chirp: Low Power/Cost Modem=>All Available Pigeons=>Globally Contiguous Clouds=>Massively Scalable.
Edge Intelligence. The rapidly accelerating confluence of
Distributed AI with Software Defined Networking (SDN) prompted
a shift to Cloud->Edge thinking where networks
coalesce as
logically contiguous
across walled gardens - Global Scale Edge Intelligence. See these
Slides.
Small, Dumb,
Cheap, Copious types of Connectivity then drives new
- and currently unimaginable - efficiencies. |
||
|
|
||