Anchor
Glossary
One Page Primer
Slides Soft ChipsTM Blogs
Book
Mesh ACG
SlideShare
Linkedin Bio
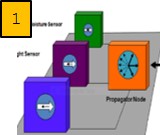

Fig. 1. Soft Chip
TM Trusted
Sensor Patch -> Data Logs -> Pigeons ->
Cloud -> Actionable
Edge Intelligence
 Rationale for Soft ChipsTM
Rationale for Soft ChipsTM
Chirp protocols are generic and intentionally rudimentary-
they can run on any radio and coexist with any existing
protocol. When Chirps are detected, Chirp protocol handlers
run - in the phones or on USB modems. Simple ant-like edge
intelligence is imprinted to provide When-this-then-that and
If-when-this-then-that processes. Soft Chips - as the same
suggests, can have their behaviors modified. Suites of sensors
can be activated by imprinted code to perform specific tasks
using specific sensors e.g. make data logs, relay "fire!"
alerts, corroborate multi-sensor feeds. Soft Chips may be made
in millions because they support multiple use cases and are
future proof- because of the radio and protocol agnostic
nature of Chirps.
Intended benefits of these embodiments are in them being:
|
.
Small
. Dumb
. Cheap
. Copious
. Secure
. Custom
. Agnostic |
Small Radio Power Usage
and Footprint - Long Battery life.
Limited Ant-like processing capabilities - but re-programmable.
Intended to be produced in millions - since multi-use.
Intended to be used like seeding crops - deep ground
truth verification.
Imprinting process - end-to-end - is innately secure. USB
modems add security.
No central standards committee needed. Modem based
Chirp protocol custom.
Chirps are radio and protocol agnostic. Can coexist
with other protocols. |
 Example:
RFID++: Low Cost Asset Status Trackers.
Example:
RFID++: Low Cost Asset Status Trackers.
Consider
RFID - a static
GUID identification scheme. Tags are applied to boxes in
transit. When energized, they transmit a static code to
RFID readers.
RFID++
tags - can be active tags
attached to provide travel logs from sensors - temperature,
sound & accelerometers - and
imprinted by Enterprises for specific
SLA compliance verification and monitoring.
These specific travel Logs are released to
Carrier Pigeons (the iterant readers) when
imprinted handshakes are sent to sensors on the chip to
wake up and
Chirp. Minimal power consumption is due to both the
cryptic 1-2 bytes payloads vs.
IPV6 40+ bytes and that transmission are scheduled -
managed
RF interference.
Chirp protocols are thus efficient.
MAC based
CSMA/CA protocols are inherently inefficient for these
reasons.
This managed
Collision
Avoidance - in both time and RF Space - is
the
Cloud Orchestrated Model.
Establishing provenance of sourced materials - which
wood came from which forest - comes from imprinted tags that
follow the felled tree from the forest to the lumber yard.
Provenance Trust chains begin when the tree is first felled
and an
RFID++ tags is attached to it.
RFID++
thus establish sourcing for regulatory agencies and also
provide a record of travel conditions e.g.
SLA compliance on perishables.
 Soft ChipsTM
and its Multi-Use Cases (military and industrial).
Soft ChipsTM
and its Multi-Use Cases (military and industrial).
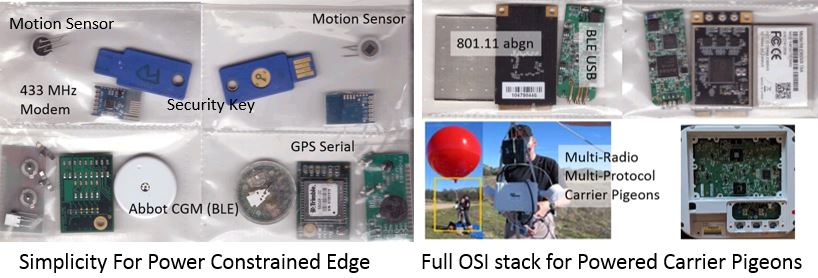
Fig. 2. Serial Modems
are small dumb cheap copious. Ubiquitous Carrier pigeons
serve as transports.
Soft Chips have a minimal - but extensible - base vocabulary: Send,
Listen, Relay, Log. Transmissions are either scheduled - e.g.
Cron
- or trigged by events - a listener on activated sensor on
Chirp Chips.
This Extensible Soft Chips family addresses multiple military
and industrial -
dual use - applications.
1. RFID++
RFID is a static
GUID identification scheme. The tags is applied to boxes
in transit and when energized, transmit a code to the reader.
Similarly, a RFID++ tag is an active tag applied to perishable
items, for example. It builds a data log of the item in
transit - based on packaged Infra-red, temperature, sound &
accelerometer sensors activated selectively to address purpose
driven
SLA compliance requirements.
2. Chirper GridTM - Aerial sensor dusting of large areas
for forest fires running in relay mode. As soon as any heat
sensor is triggered, it is relayed - the entire region lights
up. Any carrier pigeon, intermittently servicing the region
sends the alert. A version for intrusion detection uses
vibration and sound sensors (microphones).
3. Sensor PatchTM For Legacy Edge assets - remote pump motors
- may now have a non invasive sensor logging service providing simple predictive maintenance- driving new
efficiencies in servicing legacy assets. Gas pipe leakage
detection, air and ocean pollution sensors may be copiously
deployed -
Smart Dust.
4. Military versions - covert mobile asset tracking and intrusion detection in
DMZ
or hostile regions.
5. Modem Chipset only - not packaged with sensors,
providing a serial bus interface to Enterprise sensor patch -
without the wireless communication unit. Based on simplified
FREERTOS and
Sub-1
GHz radios (for range and leverage less congested RF). Soft Chips may customize this
Exemplary Soft Chip Work Flow to harvest edge data
securely.
 Soft ChipsTM
and
CHIPS initiatives.
Soft ChipsTM
and
CHIPS initiatives.
Soft Chips embodiments are intended
for dual use (military and industrial) since the security is in
the imprinting services provided by trusted hosted services.
The two ends of wireless modem have to
"match" or know of each others' schedules and RF channel usage
and handshake protocols.
End-to-End and
zero trust.
In our polarized world, governments and military deploy edge
devices
imprinted by them to provide womb-to-tomb ground
truth verification. Sensitive data is not sent over foreign
networks and equipment. Covert networks over trusted devices
are used. Business is war watered down. Today, all Global
enterprises and Regulatory agencies run on federated “Clouds”
and expect authentic data from their assets on the ground.
CHIPS initiatives - "integral to America’s economic and
national security" benefit from collaborative sharing of
trusted, previously
walled private gardens. Globally Relevant
challenges are now addressable.
Global scale challenges mandate Globally Relevant Edge à Cloud
solutions.
 Soft ChipsTM and
Upgradeable
COTS products.
Soft ChipsTM and
Upgradeable
COTS products.
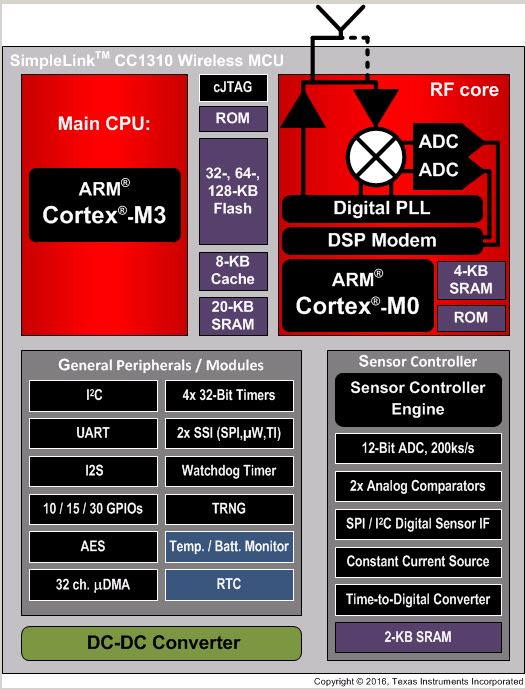

Fig. 3. Exemplary Sensor Package Development tool kit, COTS
Sensor Controller and Sensors. Click for more.
In 2016 a developer implemented a version of Chirps
on
Raspberry PI with a two byte Chirp. Web
We now take this to the next level – innately secure, cloud
orchestrated Cloud->Edge messaging.
Texas Instruments and others US Chip makers provide extensive
Sensor Controller development environments. The
Sensor Controller Studio, for example, supports a plethora
of radios - all of which can be Chirp aware.
These MAC based radios need a simple protocol handler, running
at the
Lower Level MAC, to detect Chirps.
These radios are already on - Ubiquitous - carrier
pigeons and run the full OSI stack. In those cases, where a
specialized radio is needed, a USB attachment - Enterprise
Imprinted - is a simple fix.
Long range
Sub-1
GHz radios are used by
Amazon Sidewalk. With Chirp
extensions this network extends to farms and forests -
Sustainable Global Impact. Military deploy
Software Defined Radios - easily Chirp aware.
 Soft ChipsTM and
Our Supervised Autonomy Bias
Soft ChipsTM and
Our Supervised Autonomy Bias
In 1992 a
Supervised Autonomy Architecture (video)
was deployed in multiple
dual use cases.
In 2003 Soft ChipsTM Concepts were developed for
Military stealth intrusion detection. It became apparent that the last mile connectivity
for remote assets had its
challenges and needed resolution first. Mobility, Scalability, Terse messaging and
Logically Contiguous Clouds were addressed first. Chirps
were first discussed
here
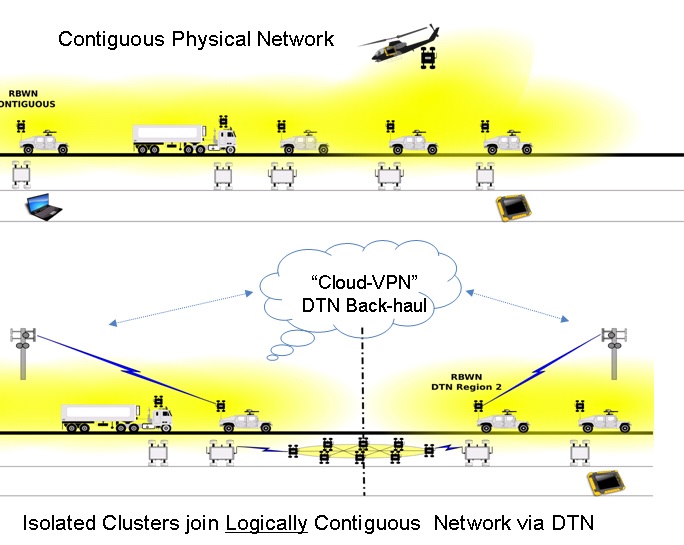
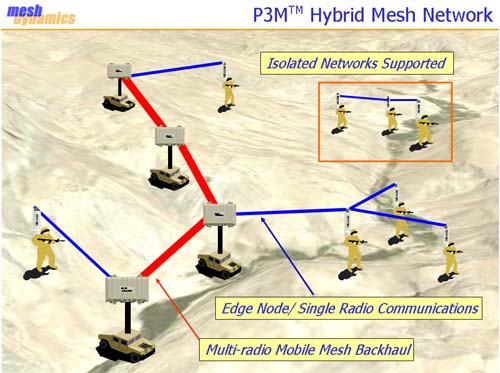
Fig. 4. Logically Contiguous Remotely Managed, robotic
devices.
Animation.
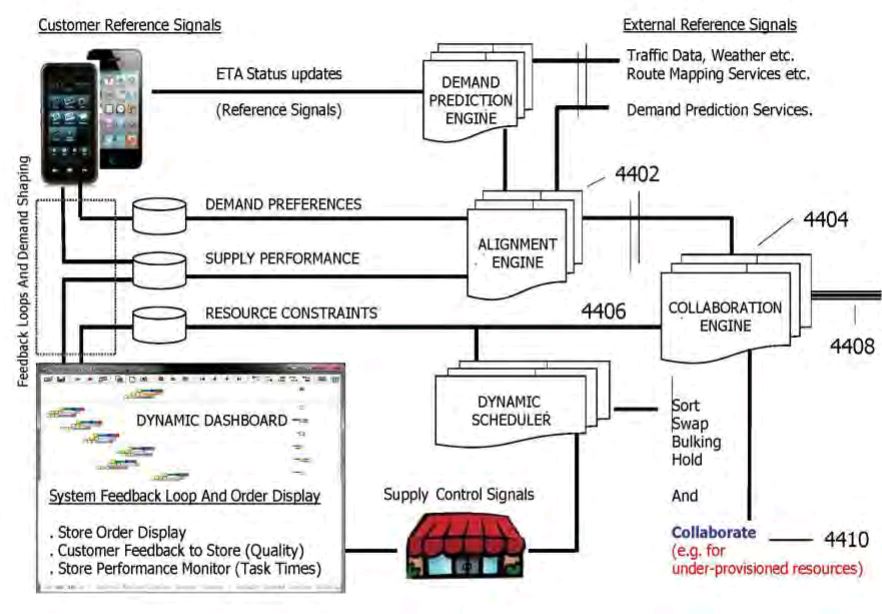
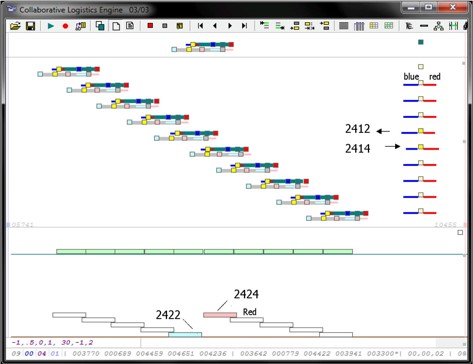
Fig. 5. Task delivery constraints aligned with subscriber
demand and task delivery schedules.
Animation
 Soft
Chips Summary and Conjectures.
Soft
Chips Summary and Conjectures.
The rapidly accelerating confluence of
Distributed AI with Software Defined Networking (SDN) prompted
this Cloud->Edge thinking.
Cheap, Copious, Global Scale Connectivity then drives new -
currently impractical - efficiencies.
Soft Chips is a "natural" alternative to key challenges in
remote edge asset management.
Bio Slides.
1. Today: Edge with
BLE,
Zigbee,
Lora
=> Fractured Markets and Silos ==
Not Massive
versus
2. Chirp: Edge with Imprinted Pigeons
=>
Contiguous Clouds and
Pub/Sub ==
Massive and Trusted.









